TL;DR:
- Impact analysis is a structured process for evaluating the consequences of a change before you make it — basically a pre-flight checklist for technical work.
- The 5-step framework: define the change, identify dependencies, determine blast radius, create a rollback plan, and communicate with stakeholders.
- Without it, you're gambling. With it, change becomes strategy — fewer outages, faster recovery, and way more trust from leadership.
Every Salesforce administrator has a war story about a “small” change that went spectacularly wrong.
Maybe it was a developer swapping out a single API parameter, an admin deactivating something that looked like an unused field, or a RevOps leader tweaking some lead routing rules.
On paper, the change was trivial. But in practice, it triggered a chain reaction: integrations failed, dashboards broke, sales reps couldn’t enter opportunities, calls were made, and leadership demanded to know what happened.
What happened, simply, was a lack of foresight.
In complex systems, nothing truly lives in isolation. A minor adjustment in one corner can ripple out in unexpected ways — what’s often called the blast radius of change. That ripple effect can cost teams hours of panic-driven work, thousands in emergency fixes, and even millions in lost revenue.
This is why professional operators use impact analysis.
Think of impact analysis as the structured process of evaluating the potential consequences of a proposed change before making it.
It’s basically like a pre-flight checklist for technical change.
Just as pilots don’t take off without systematically verifying every critical system, technical teams shouldn’t deploy a change without exactly understanding its downstream effects. Impact analysis helps you find hidden dependencies, assess risks, plan mitigations, and communicate clearly with stakeholders before anything goes live.
In this guide, we’ll cover:
- Why impact analysis is a non-negotiable in modern tech environments.
- A practical five-step framework any team can adopt.
- Real-world examples of how impact analysis works across domains like software development, infrastructure, and business operations.
- Links to deeper “spoke” guides on applying these principles to specific platforms, like Salesforce.
By the end, you’ll understand what impact analysis is, and also how to put it into practice as a core discipline in your change management process.
Why impact analysis is non-negotiable
Every modern technical team is in the business of change. Especially now, as AI continues to add complexity to systems. Deploying new features, adjusting workflows, refining data models, swapping out integrations… these are the gears that keep organizations competitive.
But every change also carries risk. And in today’s interconnected tech ecosystems, a misstep can hurt dozens of teams and systems.
The stakes of getting it wrong
- Downtime costs money: According to 2014 Gartner study (and a Ponemon Institue study that backed it up not two years later), the average cost of IT downtime is over $5,600 per minute. That’s more than $300,000 an hour — and higher for industries like finance or healthcare where service interruption is mission-critical.
- Emergency fixes drain morale: One Friday afternoon change can lead to a weekend of nightmarish firefighting, creating burnout and damaging trust in the team.
- Leadership notices failures, not smooth sailing: Executives rarely applaud “nothing broke.” But one unplanned outage can erode confidence in IT, RevOps, or DevOps leadership overnight.
Real-World examples of poor change management
- Knight Capital, 2012: A software update triggered old, dormant code. In 45 minutes, the firm lost $440 million, forcing it into a fire sale.
- Healthcare EHR downtime: Hospitals have reported system outages during EHR upgrades that forced a return to paper records and risked patient safety.
- Retail e-commerce failures: Schema changes in product databases have taken checkout systems offline during peak shopping seasons, costing millions in lost revenue.
Those are not edge cases right there.
They’re, unfortunately, the predictable results of deploying change without understanding the impact.
The payoff of doing it all right
Impact analysis turns this gamble into a professional discipline. Teams that practice it consistently see:
- Reduced risk: By finding those dependencies before they blow up, problems are prevented instead of patched over.
- Predictability: Changes fit smoothly into the software dev lifecycle, with fewer surprises in QA or prod.
- Faster progress: Ironically enough, slowing down to assess impact makes teams move faster overall — mostly just because they avoid costly rework.
- Trust from leadership: Nothing builds credibility with executives like confidently explaining the scope, risk, and mitigation plan of a proposed change.
Without impact analysis, change is gambling. With it, change becomes your strategy. And it’s a tremendous strategy to have.
The 5 steps of effective impact analysis
Alright, as we discussed earlier, think of this pre-flight checklist for technical change. Each step ensures you’re not flying blind into the future, making some mistake that puts you on your boss’s radar (in the bad way).
Step 1: Define the proposed change
The most common mistake is starting impact analysis without first writing down precisely what you intend to change. Vagueness here will impact the rest of the process. Here’s the three things you’ll need to include in your analysis.
- Definition: Be precise about the scope. Are you adding a new field, adjusting a microservice, modifying a workflow, or swapping an integration?
- Tools: Change request templates in Jira or ServiceNow. Even a shared doc works if it’s consistent.
- Roles: The change owner (developer, admin, or ops lead) should draft it; reviewers validate scope.
Example: Instead of “update CRM workflows,” write “add a new validation rule preventing duplicate phone numbers in the Lead object.”
🪄 Magic tip: If you can’t explain the change in one or two sentences, it’s likely too broad. Break it down further.
Step 2: Identify potential dependencies
Tech systems are like spiderwebs. If you tug on one strand and others shake. This is where the real detective work starts.
- Definition: Catalog everything connected to or relying on the system you’re changing.
- What to include:
- Data models and schema relationships
- Automations, scripts, and workflows
- Third-party integrations and APIs
- Reporting layers and any relevant dashboards
- Upstream and downstream business processes
- Tools: Dependency mapping tools (Lucidchart, Miro), application performance monitoring (New Relic, Datadog), Salesforce’s schema builder
- Roles: System admins, architects, and integration specialists.
Before deactivating a “Discount Code” field, check whether it’s used in pricing logic, downstream invoices, or quarterly revenue reports.
🪄 Magic tip: Don’t just check technical connections. That simply won’t be thorough enough. You need to ask business users how they rely on the system day-to-day as well.
Step 3: Determine the blast radius
Not all changes are equal. Some have minor impact, others are tsunamis of change.
- Definition: Estimate the scope (who is affected) and severity (how bad it could be) of the change.
- Questions to ask:
- If this fails, who will notice? (end-users, leadership, customers?)
- Will it cause minor annoyance, revenue loss, or even compliance failure?
- Is the timing risky (e.g., quarter-end, peak traffic season)?
- Tools: Risk matrices, automated testing environments, sandbox sims.
- Roles: QA engineers, business analysts, system owners.
Changing a color in the UI? Low blast radius. Updating authentication logic? High blast radius affecting every user login.
🪄 Magic tip: Use a simple 2x2 matrix (low vs. high scope and low vs. high severity) to quickly communicate your blast radius.
Step 4: Create a mitigation & rollback plan
Like jumping out of an airplane, every change should come with a parachute. You’ll want to document how you’ll minimize risk and what you’ll do if the change goes sideways.
- Mitigation strategies: Phased rollouts, feature flags, parallel testing, backup snapshots.
- Rollback strategies: Version control reverts, database restore points, toggling off a feature flag.
- Roles: DevOps, database admins, system architects.
Before deploying a new integration, set up logging and monitoring to detect errors within the first 10 minutes. If they spike, roll back to the last stable version.
🪄 Magic tip: A rollback plan is useless if it hasn’t been tested. Run a mock rollback before you ever need it.
Step 5: Communicate!
Impact analysis isn’t complete until you’ve aligned with the people who it affects. Share your findings, risks, and plans with both technical and business stakeholders in a quick one-page summary (as you may know, many GTM leaders love these).
- Roles: Change owner presents; stakeholders include IT leadership, business unit leaders, end-user reps.
Before disabling an integration, alert finance that invoices may be delayed, provide the mitigation plan, and set expectations for monitoring.
🪄 Magic tip: Speak the stakeholder’s language! Execs don't want your system logs, they want business impact framed in cost, time, or risk. (If you’re in a pinch, feed your summary to a given LLM and ask it to help you “make this information brief and stakeholder relevant for my [insert title here].”)
Types of Impact Analysis
Impact analysis isn’t just for software developers or system admins.
No, any time a change is introduced into a complex technical environment that has revenue on the line, the same principles apply: you need to map dependencies, assess risks, and prepare for contingencies.
Here are four major domains where impact analysis plays a critical role.
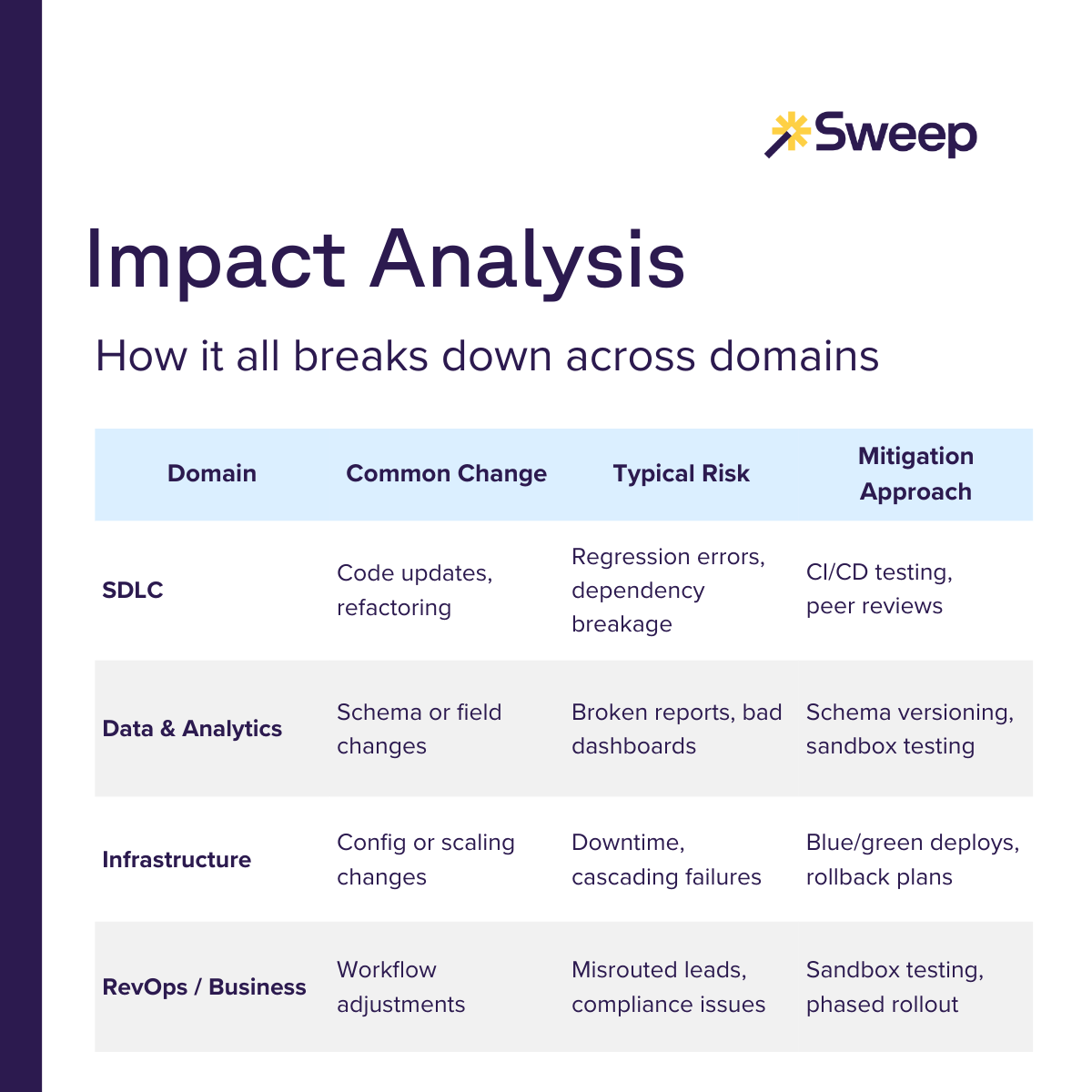
1. Software Development Lifecycle (SDLC)
- Common changes: Adding new features, modifying code libraries, refactoring modules.
- Typical risks: Regression errors, incompatible dependencies, untested edge cases.
- Mitigation approach: Automated testing suites, continuous integration pipelines, peer code reviews.
- Example: Updating a core authentication module may pass unit tests but fail in production if an external API uses legacy tokens.
2. Data & Analytics
- Common changes: Modifying database schemas, adjusting ETL pipelines, altering data fields used in reporting.
- Typical risks: Broken reports, inaccurate dashboards, data loss or duplication.
- Mitigation approach: Schema versioning, sandbox testing, monitoring queries for anomalies.
- Example: Removing a “Customer Tier” field looks harmless until you realize it’s being used to segment pricing reports for executives.
3. Infrastructure & DevOps
- Common changes: Scaling microservices, modifying Kubernetes configs, migrating workloads to new cloud providers.
- Typical risks: Downtime, cascading service failures, performance degradation.
- Mitigation approach: Canary deployments, blue/green environments, rollback scripts.
- Example: Updating a load balancer configuration causes timeouts across multiple applications during peak usage hours.
4. Business Processes & RevOps
- Common changes: Adjusting CRM workflows, modifying lead routing, changing sales compensation rules
- Typical risks: Misrouted leads, delayed invoices, compliance violations.
- Mitigation approach: Testing changes in a sandbox, cross-departmental sign-off, staged rollouts.
- Example: A new rule that prevents duplicate accounts inadvertently blocks existing integrations with customer support tools.
The big takeaway here: Yes, the details may change, but the process is always the same. As change speeds up and complexity builds up, impact analysis is a vital discipline that extends well beyond domain-specific hack. Once you learn the framework, you can apply it across any technical environment, from Salesforce to SAP.
Putting theory into practice: an example
It’s one thing to talk about frameworks, but the real power of impact analysis becomes entirely more clear when you see it in action.
Let’s walk through a scenario to put a bow on this.
A simple change, hideen consequences
Imagine a RevOps team decides to add a new required field in the CRM for “Lead Source Detail.”
The goal is simple: improve reporting accuracy. The change seems harmless — just one new field. What could possibly go wrong?
But here’s what happens when you trace the dependencies:
- The new field breaks several automation rules that didn’t account for the added requirement.
- An integration with marketing automation software fails because the new field isn’t mapped, causing leads to stop syncing.
- Sales dashboards show incomplete data because historical records don’t contain the field.
- End-users get frustrated and start creating workarounds, eroding data quality further.
What looked like a 10-minute tweak triggered an entire week of disruption.
Now let’s apply the 5 steps first
Now replay the scenario with impact analysis:
- Define the change: “Add a required ‘Lead Source Detail’ field to the CRM.”
- Identify dependencies: We list out automations, integrations, dashboards, user workflows.
- Determine the blast radius: Impacts marketing-to-sales handoff, sales reporting, and data entry.
- Mitigation: Run a sandbox test, pre-fill historical records, update automation rules before rollout.
- Communicate: Alert sales/marketing teams, provide training on the new field, and ensure leadership understands the reporting improvement timeline.
With just a few hours of structured analysis, the team totally avoids a week of desperate firefighting and frustration.
From general principle to specific application
Impact analysis looks vastly different, depending on the ecosystem.
- In software dev, it’s regression testing before a release.
- In DevOps, it’s simulating failure domains in a microservices environment.
- And in business operations, it’s validating that a new CRM workflow won’t derail downstream processes.
In a complex, oft-opaque CRM like Salesforce, changing a single flow can have massive downstream consequences — breaking automations, reports, or integrations. You can explore this specific use case in our detailed guide on how to run Salesforce impact analysis.
In the end
Change is inevitable.
Growth depends on it.
But without structure, every change is a gamble — and the stakes only get higher as systems become more complex.
That’s why impact analysis isn’t some silly nice-to-have. It is, in fact, the discipline that separates professional operators from teams (and whole businesses) who seem stuck in reactive mode.
By taking the time to:
- Clearly define changes,
- Map dependencies,
- Find the blast radius,
- Build rollback plans, and
- Communicate effectively to your team…
…you stop hoping changes won’t break things, and start knowing they won’t. And that feels great.
A maturity milestone for tech teams
Organizations that embed impact analysis into their change management process see tangible benefits: fewer outages, faster recovery times, stronger trust from leadership, and ultimately, more time spent innovating instead of cleaning up. It’s a mark of technical maturity, signaling that your team manages systems proactively rather than reactively.
The next step: modernizing this process
Manual impact analysis is a strong start, but in large-scale ecosystems, the complexity quickly outpaces what spreadsheets, checklists, or tribal knowledge can cover.
Modern tools can automate dependency discovery, map risks instantly, and visualize blast radius before you hit deploy.
That’s where Sweep comes in.
Sweep is built to give technical teams total clarity before they deploy a change — surfacing Salesforce dependencies, flagging risks, and making impact analysis a built-in step, not an afterthought.
👉 If you’re ready to move from firefighting to foresight, book a demo to see how we make impact analysis simple, scalable, and reliable.

