TL;DR
- Shipping AI like software invites rollback latency and unknown-dependency blowups that turn minor glitches into regulatory, financial, and reputational risk.
- Treat AI changes as financial-grade change management: tight governance, lineage, approvals, and real-time impact analysis — or you’ll “optimize” yourself into an audit finding.
Why “breaking things” breaks money
Traditional software failures are usually (if you're doing it right) local and recoverable.
AI failures... let's just say they propagate.
A weight tweak here, a prompt template there, and suddenly boom: wrong pricing, biased approvals, hallucinated compliance answers, or an agent that “helpfully” deletes the data it believes is redundant.
The damage goes beyond a 500 error — it creates silent, compounding drag across decisions, KPIs, and customer trust.
For CIOs, that makes AI less like a web app and more like financial infrastructure. Your posture should resemble U.S. Treasury-grade controls, not “Friday afternoon deploys.”
The multiplier effects that cost you real money
1) Rollback latency: when “Revert” isn’t instant
With AI systems, rollback extends beyond code to models, prompts, embeddings, vector stores, feature pipelines, data filters, tool permissions, and agent policies — each with versions and side effects. While you hunt for the “last good state,” bad outputs keep flowing into CRMs, ERPs, and data warehouses. That's not good.
Business impact
- Revenue leakage: misrouted leads, wrong discounting, mis-scored risk.
- Ops drag: teams firefight symptoms while drift keeps generating new ones.
- Audit exposure: you can’t prove which model did what, when, and with which data.
The guardrails every CIO should keep in mind
- Enforce atomic change sets that bundle model, prompt, and policy updates.
- Require pre-deployment impact simulations (on representative data + shadow mode).
- Maintain hot standbys for models and prompts with instant cutover, not “retrain and pray.”
2) Unknown dependencies: AI is a web, not a tree
Codebases have import graphs; AI stacks have behavior graphs—models calling tools, tools mutating data, agents invoking agents, and downstream analytics treating outputs as ground truth.
Why this multiplies risk
- Hidden coupling: a “safe” prompt change in support triage alters tags that feed churn models, which alters retention offers, which hits margins.
- Opaque lineage: without end-to-end metadata, you can’t trace bad decisions back to the exact artifact version and input context.
CIO guardrails
- Build a live dependency map across data sources, features, models, prompts, tools, and consuming apps.
- Treat metadata as a control plane: lineage, provenance, approvals, and access all enforced from metadata, not tribal knowledge.
- Require blast-radius analysis before merges: what datasets, dashboards, and workflows will change as a result of all this?
Governance is table stakes; now, operational governance wins
You already track access, retention, DPIAs, and model risk. But AI requires operational governance — guardrails that can keep up with the speed of your agents.
Operational must-haves
- Versioned everything: models, prompts, tools, policies, eval suites, datasets, embeddings.
- Policy-aware agents: “can this action execute?” checks for data residency, PII, SoD, and rate limits — before an agent acts.
- Real-time observability: structured logs (inputs/outputs/tool calls), red-flag detectors (toxicity, PII, hallucination), and SLOs for decision quality.
- Signed lineage: cryptographic or tamper-evident lineage to prove what ran where and why.
The CIO playbook: ship fast without breaking trust
1) Convert change speed to confidence speed
- Shift-left evaluations: unit-like evals for prompts and policies; regression gates for common failure modes.
- Shadow + canary by default: compare candidate vs. control on live traffic; promote only with win criteria.
- Time-boxed rollbacks: contractual “TTBR” (time to business rollback) measured in minutes, not days.
2) Make metadata your agentic control surface
- Centralize impact analysis: see affected records, flows, dashboards, and SLAs before go-live.
- Use approvals with context: approvers view lineage, eval results, and predicted blast radius—not just a diff.
- Automate documentation: every deployment emits human-readable change notes for audit and ops.
3) Govern actions, not just access
- Scoped tool permissions: agents get least-privilege actions with policy checks on each call.
- Compensating controls: auto-quarantine suspect outputs; require human validation for high-risk acts (refunds, price changes, bulk deletes).
- Dual-control for money moves: two-person integrity for workflows that change revenue, cash, or regulated data.
KPI shifts for AI (what you should actually measure)
- Decision Quality SLOs: agreement vs. expert labels, factuality rates, bias drift, action success rates.
- Governance Latency: time from policy change to enforced behavior in all agents.
- TTBR (Time To Business Rollback): minutes to restore last known-good behavior across models, prompts, and tools.
- Blast-Radius Score: number of downstream assets touched per change; goal is to trend down via modular design.
- Trust Incidents: count/MTTR of PII exposure, harmful actions, or policy violations (tracked like sev incidents).
Architecture patterns that reduce rollback pain
- Artifact registries for prompts + policies (treat them like code with semantic versioning).
- Feature and embedding stores with lineage (rebuildable by timestamp).
- Dual-write fences for high-risk targets (stage → validate → commit).
- Idempotent tool design (support dry-run, diff-only, and compensating “undo” actions).
- Blue/green for agents (route % traffic; promote only after eval + business SLOs pass).
The executive bottom line
AI will compound whatever you are — good governance compounds trust; bad habits compound loss. If your culture still celebrates “heroic shipping,” you’re one agent away from a capital V, capital E Very Expensive lesson.
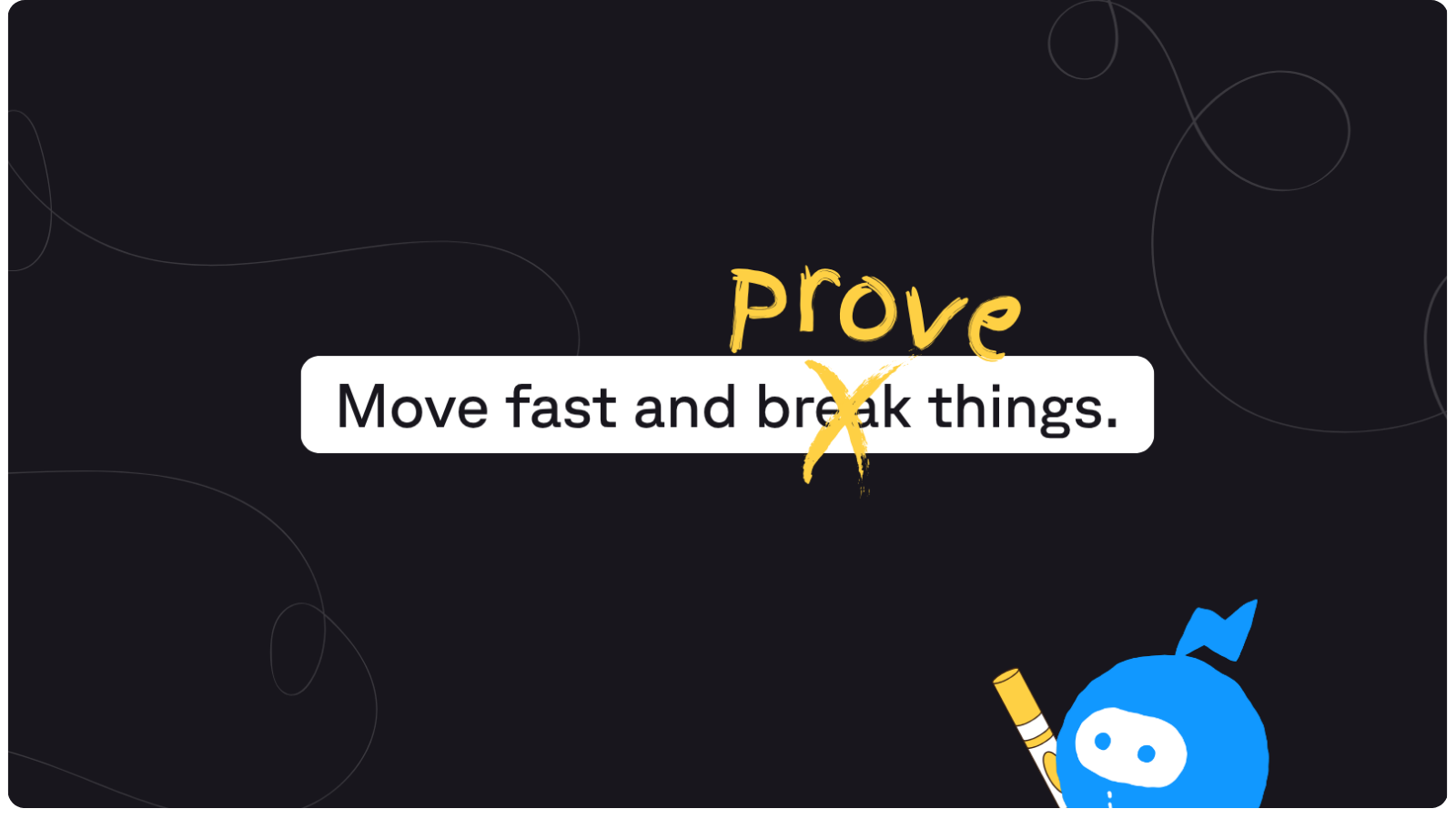
The new mandate: Replace “move fast and break things” with “move fast and prove things.” Prove impact before release, prove lineage after release, and prove you can roll back the business — not just the code — on your command.
The CIO Checklist
- Single dependency map of data → features/embeddings → models/prompts → tools/agents → consuming apps ✅
- Atomic change sets with pre-merge blast-radius and eval results ✅
- Shadow/canary pipelines and defined promotion criteria ✅
- Time-boxed TTBR and hot standby for prompts/models/policies ✅
- Signed lineage and automated human-readable runbooks ✅
- Policy-aware agents with least-privilege tool access ✅
- Decision Quality SLOs and governance latency dashboards ✅
Thankfully, there's Sweep
Sweep is the agentic workspace for Salesforce where your team and metadata agents work together to see impact before changes ship.
We maintain a live dependency map across objects, automations, and integrations; run pre-deployment impact analysis and shadow/canary evaluations; and auto-document lineage so you can cut TTBR from days to minutes.
The result: faster delivery with governance, transparency, and human oversight, not surprises.
If you’re ready to move fast and prove things, see how Sweep helps you Spot risks, Solve issues, and Stay Ahead without breaking trust.